Anyone would naturally want to utilise their systems as effectively as possible without wasting their potential. When the maximum capabilities of two components differ, it creates a bottleneck that restricts the functionality of other gear....

Humans have always produced entertainment that allows them to amuse themselves or compete with one another. Gaming is one such sort of entertainment. The term “gaming” is broad and may signify different things to different...

Do you dislike getting calls from ominous numbers? Or perhaps you’ve seen a strange number on your partner’s phone and want to figure out what it means. So stop looking now! Introducing NumLooker, your one-stop...

Considering exploring the fascinating field of web development? Dynamic, interactive online apps that attract consumers and offer seamless experiences are crucial nowadays. However, building such web apps requires a strong framework. Now that so many...

Anime art has grown in popularity over the years, enticing viewers worldwide with its distinct aesthetic and dynamic characters. As technology advances, artists and fans now have access to a wide choice of tools built...
IPTV (Internet Protocol Television) Is a digital television broadcasting system that delivers TV channels and information through the Internet. There are several IPTV service providers accessible globally, with the following being among the most popular:...

A transceiver is essential for sending and receiving data in networking and telecommunications. Transceiver, a name that combines the words transmitter and receiver, denotes the device’s dual capability. It functions as a bridge between numerous...

Scientists develop new drone technology due to technological improvements for various labour forms. Drones are beneficial for operations in both industrial and agricultural settings. You should be aware that they are guided by an automated...
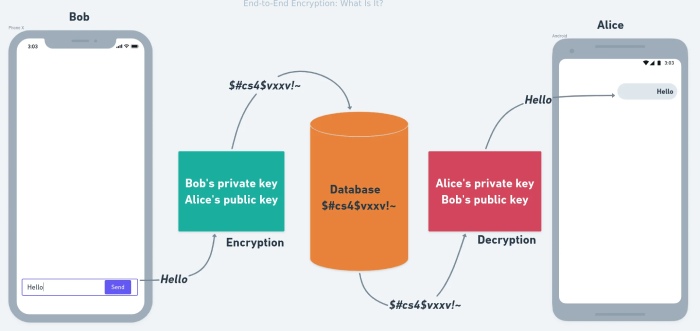
Most current messaging service providers use end-to-end encryption on their platforms. (Among others, WhatsApp, Zoom, and Facebook) Although “encryption” conjures up images of reliable cybersecurity, what does end-to-end encryption entail? Data that has been encrypted...

In the past, we kept track of working hours using time sheets. However, things are changing, and technology has made great strides; as a result, employee time-clocking applications are now a shared resource in contemporary...









