
A transceiver is essential for sending and receiving data in networking and telecommunications. Transceiver, a name that combines the words transmitter and receiver, denotes the device’s dual capability. It functions as a bridge between numerous...

Scientists develop new drone technology due to technological improvements for various labour forms. Drones are beneficial for operations in both industrial and agricultural settings. You should be aware that they are guided by an automated...

The biggest online retailer in the world, Amazon, has emerged as a well-liked venue for dropshipping, in which vendors display goods without actually keeping stock. Dropshipping on Amazon may be successful, but it takes careful...

The variety of digital marketing strategies at your disposal may be overwhelming if you are a relatively young entrepreneur or are in the process of scaling your organization. How do you even start? For instance,...
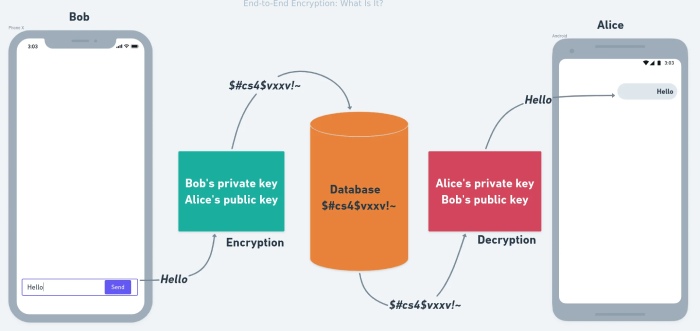
Most current messaging service providers use end-to-end encryption on their platforms. (Among others, WhatsApp, Zoom, and Facebook) Although “encryption” conjures up images of reliable cybersecurity, what does end-to-end encryption entail? Data that has been encrypted...

In the past, we kept track of working hours using time sheets. However, things are changing, and technology has made great strides; as a result, employee time-clocking applications are now a shared resource in contemporary...

One of the quickest, simplest, and most effective methods to connect with new clients is through email marketing software solutions. Email personalization, design flexibility, cost-effectiveness, segmentation, A/B testing, and scalability are just a few advantages...

Anyone with a computer and an internet connection may now participate in online dating, enabling relationships between individuals that were before impossible. Online dating, while a great way to meet individuals who share your interests,...

We like displaying and picturing ourselves in many ways as digital citizens. And if new technologies that might help us with this are available, we want to try them all. The most current trend in...

Insider threats mitigation requires teamwork. Combining the various tools, methods, technologies, and strategies builds a network of defenses that detects and stops instances of illicit insider behavior. Knowing your data, having rules requiring users to...









